On November 4, 2025, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) announced a new round of sanctions targeting multiple North Korean bankers and financial institutions. The action freezes all assets of eight individuals and two entities within the United States or under U.S. jurisdiction. These individuals and entities are accused of raising funds for the North Korean regime through cybercrime, information technology (IT) labor fraud, and other illicit activities, with the proceeds supporting the country’s nuclear and ballistic missile programs.
Sanctions Details
According to the U.S. Department of the Treasury, the North Korean government has long relied on a variety of illicit activities, including cybercrime, to fund its weapons of mass destruction and ballistic missile programs. The regime directs its hackers to profit through cyber-enabled espionage, disruptive cyberattacks, and financial theft. Over the past three years, North Korea-linked cybercriminals are reported to have stolen more than USD 3 billion, primarily transferred in the form of cryptocurrencies.
At the same time, a significant number of North Korean IT workers conceal their nationality and identity by registering accounts on freelance platforms and using false or stolen information when applying for contracts. They carry out a wide range of IT development work, earning hundreds of millions of dollars annually. In some cases, they collaborate with foreign programmers on projects and share the proceeds.
OFAC emphasizes that North Korea is able to move and launder these illicit proceeds through the international financial system by relying on a network of international financial institution representatives, composed of domestic and foreign bank agents, financial institutions, and shell companies. These intermediaries, located in multiple countries including China and Russia, provide North Korea with access to global markets and financial channels, enabling the regime to generate funds through fraudulent IT work, digital asset theft, and sanctions evasion.
The sanctioned targets include:
1. Entities (2):
Ryujong Credit Bank — A financial institution headquartered in Pyongyang, North Korea. The bank has provided financial services facilitating sanctions evasion between China and North Korea, including the remittance of North Korea’s foreign currency earnings, money laundering, and financial transactions for overseas North Korean workers.
Korea Mangyongdae Computer Technology Corporation (KMCTC) — An IT company headquartered in Pyongyang, North Korea, reportedly operates IT worker dispatch operations in at least two Chinese cities — Shenyang and Dandong. KMCTC’s IT workers have used Chinese nationals as banking proxies to conceal the true origin of funds generated through their illicit revenue-generating activities.
2. Individuals (8):
Choe Chun Pom — A representative of the Central Bank of the DPRK in Russia. He has facilitated transactions worth over USD 200,000 in both U.S. dollars and Chinese yuan and coordinated travel arrangements for Russian officials visiting Pyongyang.
Han Hong Gil — An employee of Koryo Commercial Bank Ltd, who coordinated over USD 630,000 worth of transactions in U.S. dollars and Chinese yuan on behalf of the sanctioned Ryujong Credit Bank.
Jang Kuk Chol and Ho Jong Son — Fund managers at First Credit Bank. They managed overseas funds exceeding USD 5.3 million, including crypto assets traced to DPRK-linked ransomware groups and IT labor networks. They were sanctioned for “providing financial and technical support to cybercrime operations.”
Ho Yong Chol — A China-based North Korean financial representative who facilitated the transfer of more than USD 2.5 million in U.S. dollars and Chinese yuan on behalf of Korea Daesong Bank, and managed transactions worth over USD 85 million for another DPRK government-affiliated organization. He was designated for “acting on behalf of sanctioned banks” and helping the DPRK financial system evade sanctions.
Jong Sung Hyok — Chief representative of the sanctioned Foreign Trade Bank (FTB) in Vladivostok, Russia, responsible for facilitating cross-border settlements and money-laundering activities for the bank.
Ri Jin Hyok — A representative of FTB, who facilitated transfers exceeding USD 350,000 in U.S. dollars, Chinese yuan, and euros on behalf of an FTB front company.
U Yong Su — Current head of KMCTC, designated for managing the company and engaging in overseas IT labor and money-laundering activities.
These eight individuals form the core of the DPRK’s financial representative network in China and Russia, providing channels for fund transfers, account management, and money-laundering services in support of North Korea’s illicit activities.
Sanctioned Address Analysis
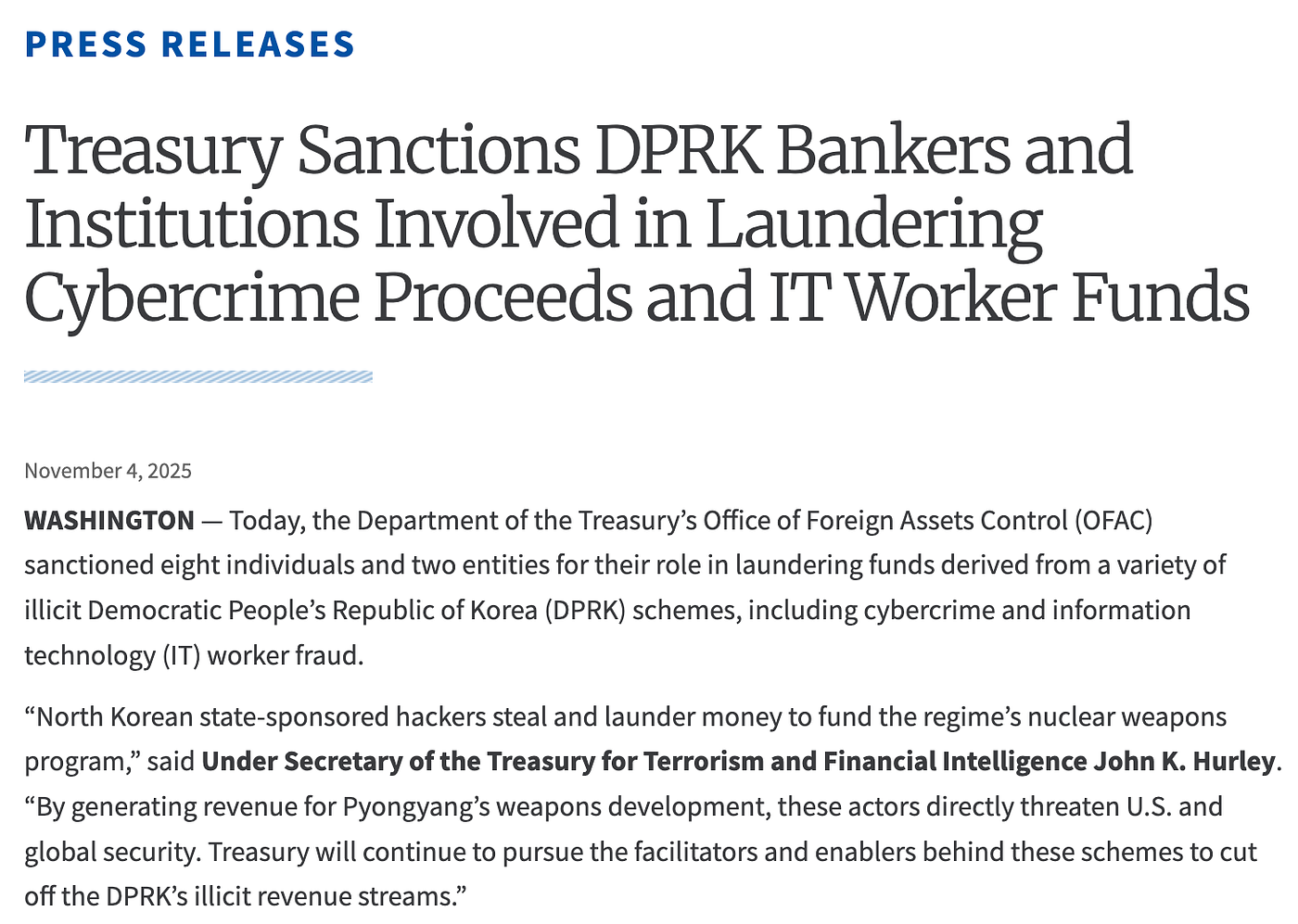
In addition, when updating the SDN List, OFAC identified 53 cryptocurrency addresses associated with Cheil Credit Bank.
We conducted an analysis of the 53 USDT-TRC20 addresses included in the sanctions list using MistTrack, SlowMist’s on-chain tracing and anti-money laundering (AML) tool. The analysis revealed the following:
Get SlowMist’s stories in your inbox
Join Medium for free to get updates from this writer.
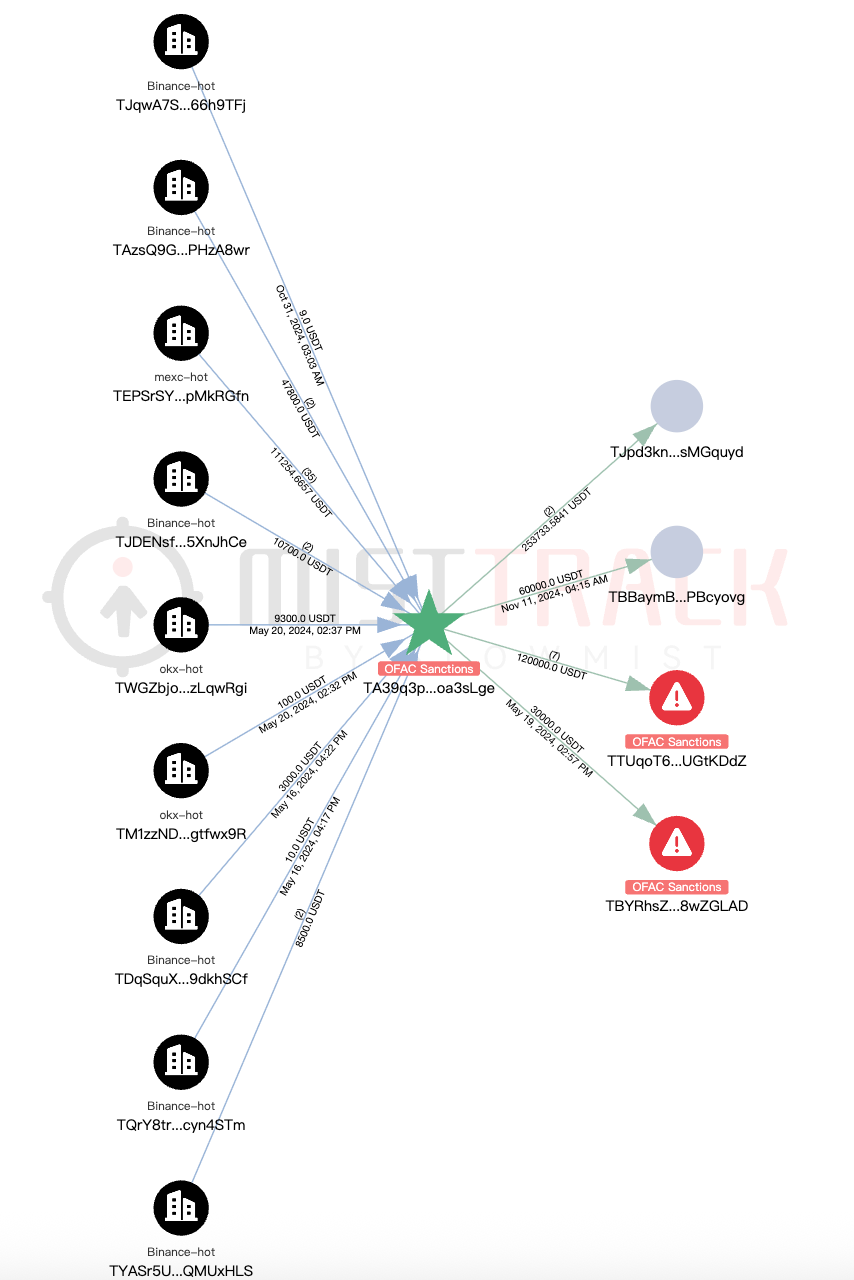
These 53 addresses have collectively received approximately 16 million USDT-TRC20. The sources of funds are primarily concentrated in hot wallets of several major exchanges, with a portion also traced back to previously sanctioned addresses involved in other incidents.
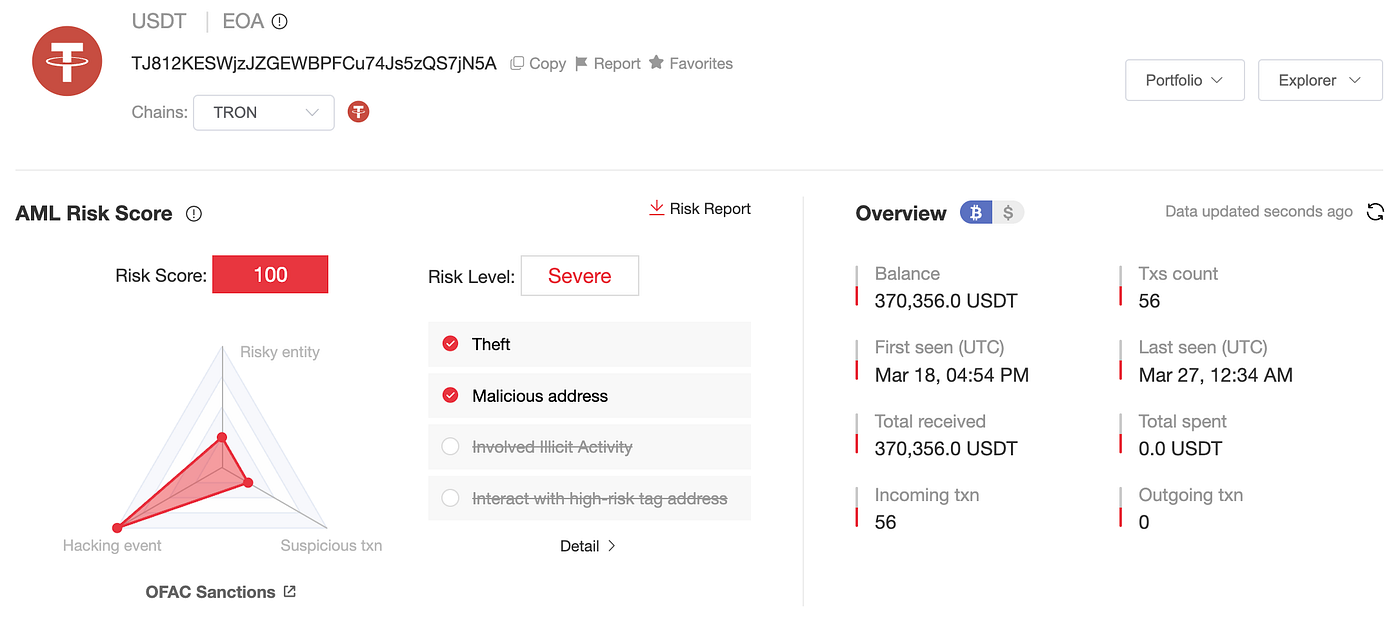
As of now, approximately 60% of the addresses have a zero balance, indicating that the funds have already been moved or laundered. The remaining 40% of the addresses still hold balances ranging from 270,000 to 380,000 USDT each, with a total of around 6.5 million USDT. All of these funds have been frozen by Tether.
In terms of activity period, transactions involving these 53 sanctioned addresses spanned from August 2023 to July 2025, with the most concentrated activity occurring between mid-2024 and the first half of 2025. From January to May 2025, transaction volume remained high — particularly in May, when multiple transactions occurred almost daily. A few addresses were only active for short periods, ranging from a few days to a week (e.g., May 6–7). Activity dropped sharply after early August, and most addresses ceased new transactions about a week before the sanctions were announced.
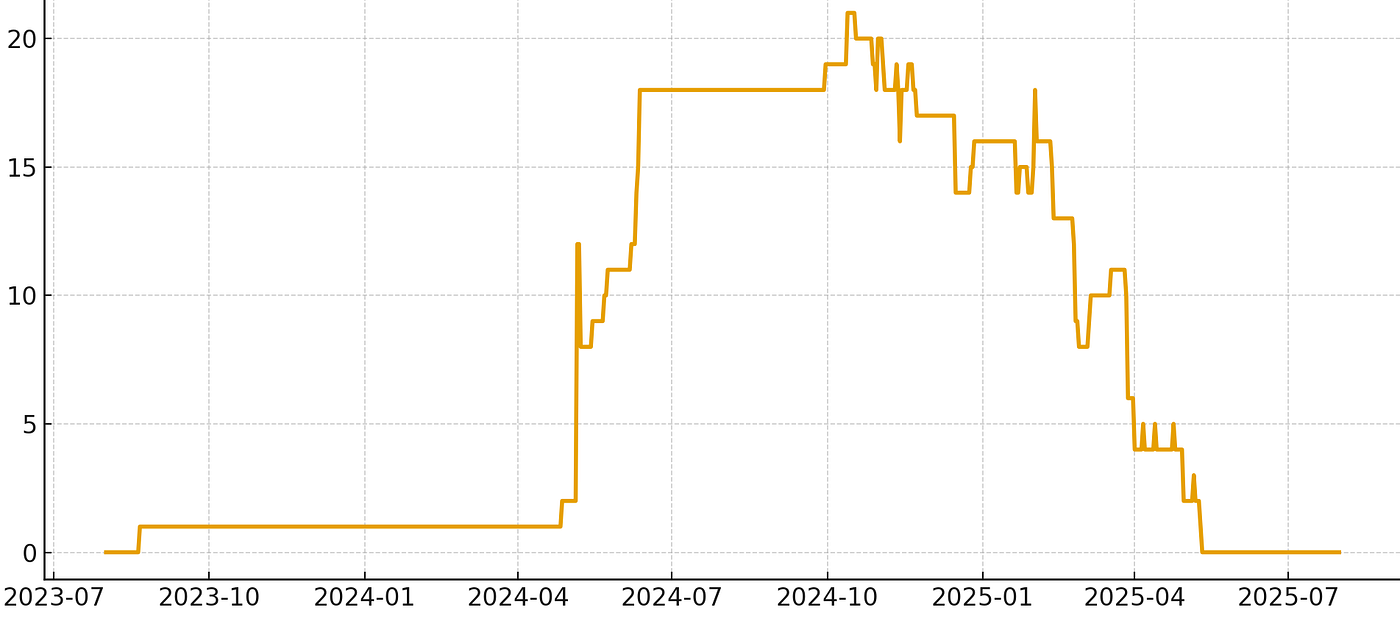
In terms of transaction paths and frequency, we observed clear patterns of multi-stage transfers and cross-convergence among the addresses. For example, addresses such as TGKgL, TGpNz, TQKQ4, and TXFUY engaged in repeated back-and-forth transfers, which we assess were likely intended to obscure the origin of funds and to complicate the tracing of their movement.
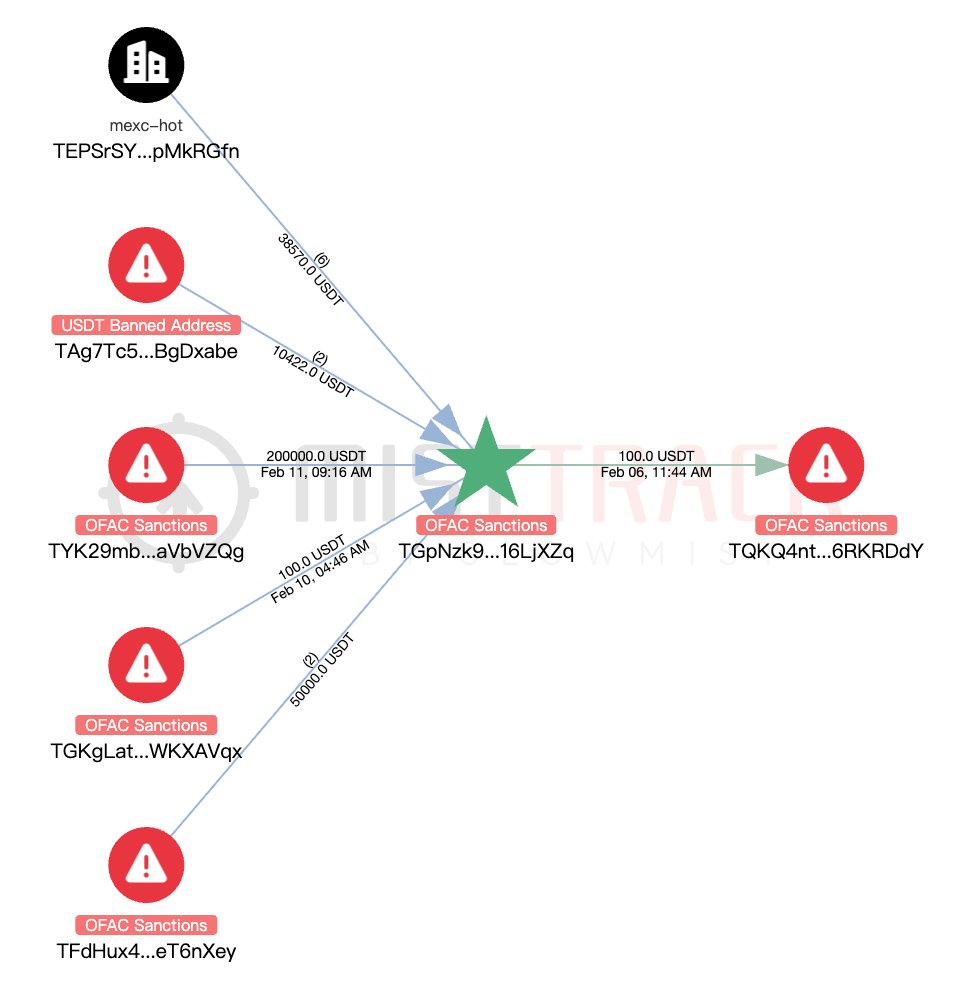
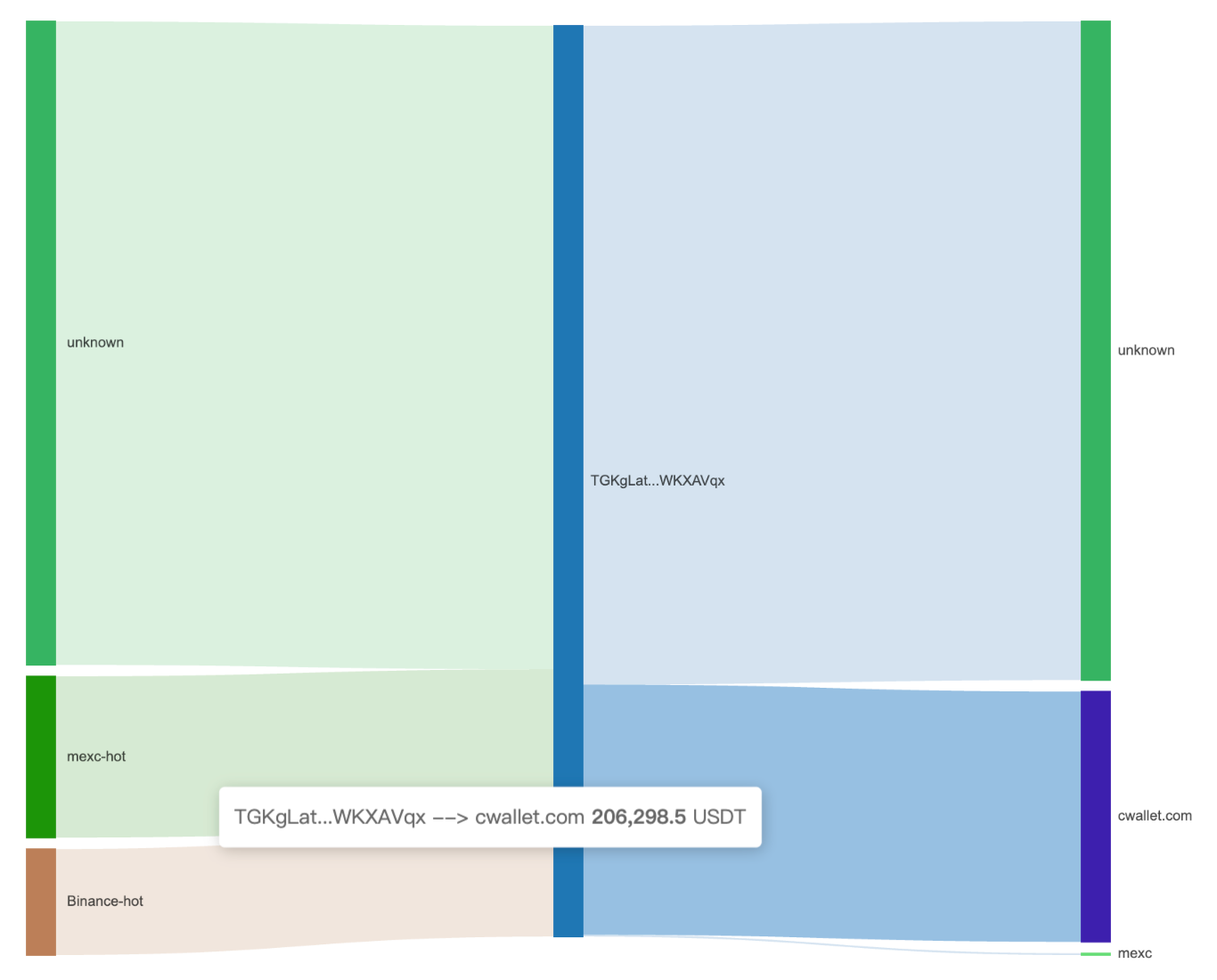
In addition, several addresses (such as TGKgL, TBwghb, and TMECK) have deposited or transferred funds to platforms including Binance and MEXC.
AML Recommendations
This round of sanctions highlights the risks posed by North Korea’s use of cybercrime, IT labor fraud, and an international network of financial representatives to raise funds and evade sanctions. To mitigate these risks, practitioners should screen counterparties’ on-chain addresses in real time — using on-chain tracing tools such as MistTrack — before accepting or transferring digital assets. Conduct due diligence into historical transaction behavior and potential red flags, verify that funds’ origins are transparent and compliant, and avoid receiving assets from sanctioned wallets, known high-risk addresses, or suspicious transaction paths. Meanwhile, businesses, exchanges, service providers, and other project operators should implement robust customer identification (KYC) and on-chain transaction monitoring (KYT) procedures, continuously trace fund flows, identify potentially high-risk addresses, sanctioned entities and suspicious funds, and avoid business relationships with high-risk parties to reduce the chance of being unknowingly entangled in sanctionable networks or illicit fund flows.
Drawing on years of blockchain security research and risk-control practice, SlowMist’s on-chain AML tracing and analysis system, MistTrack, has provided reliable on-chain risk monitoring and strong AML compliance solutions to numerous exchanges and enterprises, and delivers precise data analysis, real-time risk monitoring, and comprehensive compliance support for individual users, corporate teams, and developers. MistTrack can detect fund origins, screen whether funds originate from sanctioned wallets or high-risk addresses to prevent receipt of contaminated assets, and perform pre-transaction address checks to reduce the risk of asset freezes. To date, MistTrack has accumulated over 400 million address tags, tracked 1,000+ entities, collected 500,000+ threat-intelligence records, and identified 90 million+ risk addresses, forming a solid foundation for digital-asset security and anti-money-laundering efforts.
For more on practical on-chain AML implementations, see our prior case study: Case Study: MistTrack Empowers Virtual Asset Funds to Achieve AML Compliance and Risk Control. For more information or to experience the platform, visit: https://aml.slowmist.com.
Related links
https://home.treasury.gov/news/press-releases/sb0302
https://ofac.treasury.gov/recent-actions/20251104
About SlowMist
SlowMist is a threat intelligence firm focused on blockchain security, established in January 2018. The firm was started by a team with over ten years of network security experience to become a global force. Our goal is to make the blockchain ecosystem as secure as possible for everyone. We are now a renowned international blockchain security firm that has worked on various well-known projects such as HashKey Exchange, OSL, MEEX, BGE, BTCBOX, Bitget, BHEX.SG, OKX, Binance, HTX, Amber Group, Crypto.com, etc.
SlowMist offers a variety of services that include but are not limited to security audits, threat information, defense deployment, security consultants, and other security-related services. We also offer AML (Anti-money laundering) software, MistEye (Security Monitoring), SlowMist Hacked (Crypto hack archives), FireWall.x (Smart contract firewall) and other SaaS products. We have partnerships with domestic and international firms such as Akamai, BitDefender, RC², TianJi Partners, IPIP, etc. Our extensive work in cryptocurrency crime investigations has been cited by international organizations and government bodies, including the United Nations Security Council and the United Nations Office on Drugs and Crime.
By delivering a comprehensive security solution customized to individual projects, we can identify risks and prevent them from occurring. Our team was able to find and publish several high-risk blockchain security flaws. By doing so, we could spread awareness and raise the security standards in the blockchain ecosystem.